Security Considerations for Medical Device Companies implementing Agile PLM
1. Military/Governance Requirements (ITAR)
The International Traffic in Arms Regulations (ITAR) and the Export Administration Regulations (EAR) were established by the U.S. Dept. of State to control the export of defense-related technology and services.
Specifically, all information and material related to ITAR Controlled Technology must be safeguarded from access by non-U.S. persons unless a special license or exemption is obtained from the Dept. of State.
Med Device Companies frequently fall under this category and must take steps to stay in compliance.
This requirement is met with a multi-pronged approach:
- Physical Security requirements: Data Centers must be secured against unauthorized access at the physical location.
- Network Security requirements: Systems must be secured against unauthorized access over the network.
- Inter-Network Access Management: Through a combination of User Management, Permissions Management and Visibility control, a company controls who, in the company, sees what when.
2. Project Security Concerns
While outlining the implementation of a secure Agile PLM implementation, it is just as crucial to identify potential security pitfalls in the implementation process. When granting consultants access to your systems it is important that standard practices are in place for eliminating security risks.
3. New Project Development – Confidential Nature
In any competitive and/or regulated industry, the capability to develop projects of a confidential nature while granting visibility only to individuals that have been cleared for the information is a necessity. This is accomplished through effective user and permissions management (this is be covered in more detail later in this paper).
4. Quality Systems Structure
In the heavily regulated medical industry, it’s necessary to simultaneously manage multiple ISO systems. The permissions to change related procedures are carefully managed as an extension of effective User and Permissions management in general.
5. Multiple Sites
Multiple physical locations for offices and data centers add an additional wrinkle to the Physical and Network Security concerns mentioned above and must be accounted for.
6. LDAP Infrastructure
As a general concern in terms of IT security and specifically when LDAP will be used to manage user accounts in Agile, a properly designed LDAP infrastructure must be a part of a secure Agile PLM Implementation.
7. Supplier Use of Agile
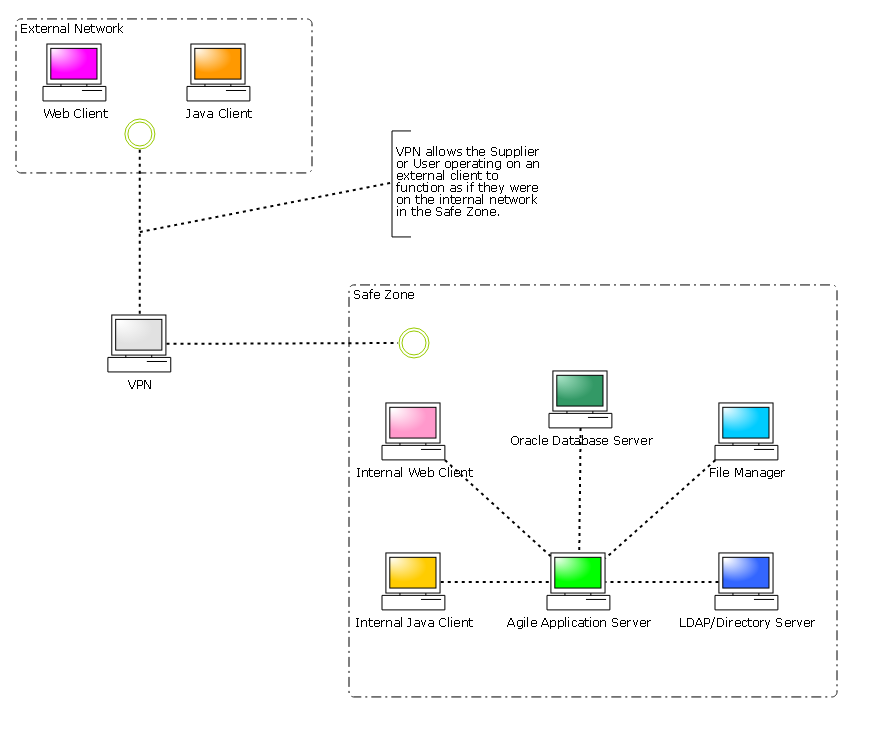
Agile PLM’s power as a collaborative tool can only be fully realized when a structure is in place that allows suppliers to access your Agile PLM while absolutely guaranteeing that they have access only to the information that is relevant to them.
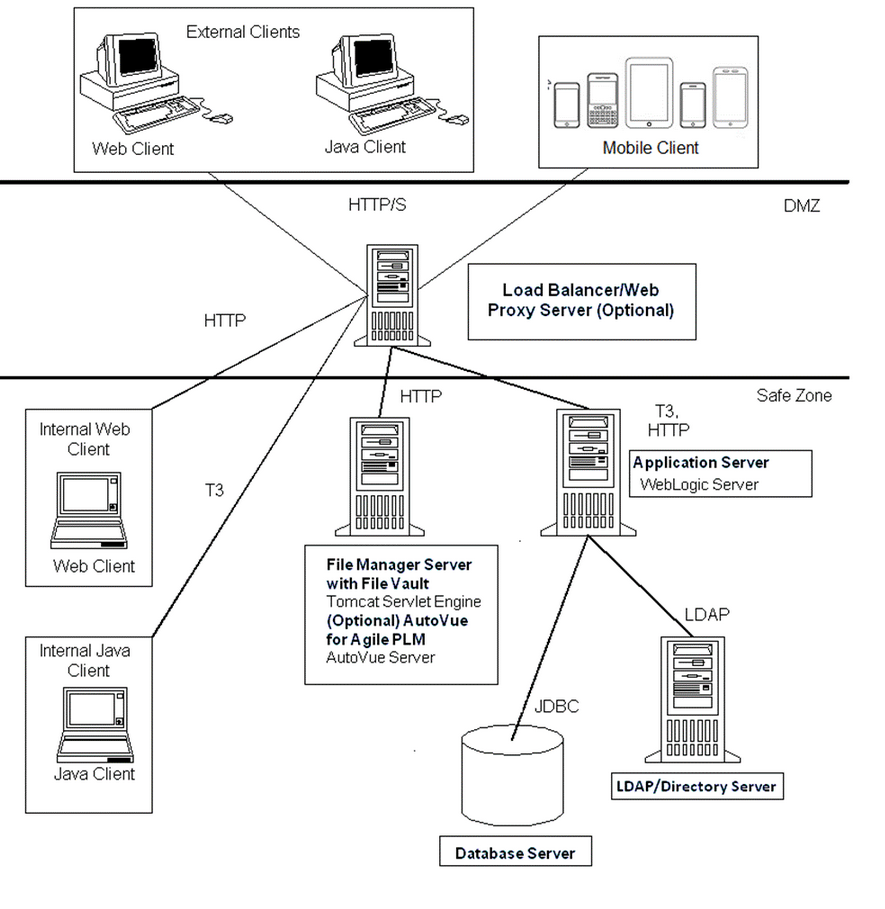
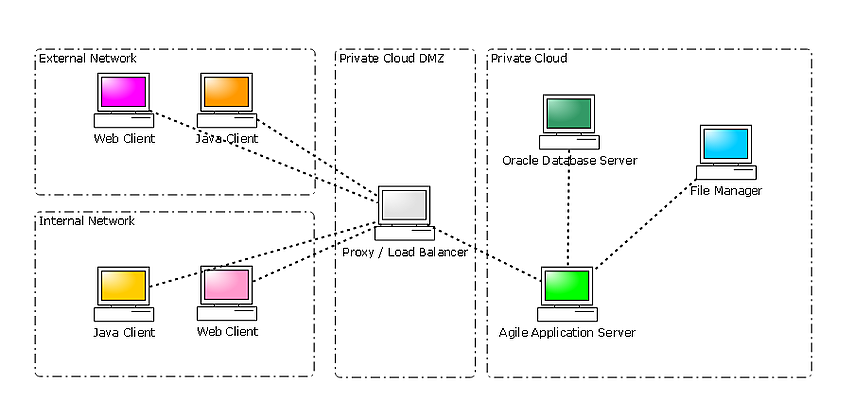
The following diagrams illustrate possible topologies for providing access to your Agile PLM system.
VPN
Proxy Server
Private Cloud
The private cloud functions in a similar manner to the proxy server option, but instead runs outside of your network in a secure, independent environment. Amazon Web Services (AWS) for instance is HIPPA certified, used by the DoD and as secure as a Proxy server.
 The best topology depends on your company’s individual business needs.
The best topology depends on your company’s individual business needs.
Best Practices for a Medical Device Company with Agile PLM
This section outlines Best Practices in User, Permissions and Process Management configuration of Agile PLM for a Med Device Company that lead to a successful secure implementation of Agile PLM.
- Have an individual log-in for each person. History is maintained on a per user basis. Knowing the actions of each person is an important part of 21 CFR Part 11.
- Require password changes on a regular basis. This is a common practices with network security programs but commonly overlooked if implemented isolated system. The password is your signature, guard it.
- Have multiple types of Admins. Separating the responsibilities to cover a larger group.
- System Admin
- Agile Admin
- Security Admin
- Data Admin
- Process Admin (Analyst)
- Permissions in agile based on the process they are performing
- Use of Roles and User Groups
- Consider each role to include in the process
- All users
- User
- Manager
- Analyst
- Admin
- Read only permissions. Data shouldn’t’ be hidden. Let people learn from CAPA and Audits.
- Only the current revision of a document should be available for manufacturing personnel. Prevent any mix-up from using old revision.
- Define a method of assigning permissions
- Typically a request to add user or Manager / Owner permissions to add people to their group or role.
- Validation as configurable system
- Validate system requirements. System requirement # 1, The configuration can change.
- Perform User acceptance testing (UAT) to verify the configuration
- Define and document the groups
- Document the purpose and tasks the group will be doing
- Document All Configuration Changes. Security and setting changes are part of the configuration.
Successful implementation of a secure Agile PLM environment can be challenging without an experienced partner. An ideal partner should have expertise in the realm of PLM, Compliance and Medical Device companies.
If you liked this blog, check out the another blog by Tim Brown titled, "A Strategy for Complying with the FDA's New UDI Ruling"
[Edit: Repost from 2014]

